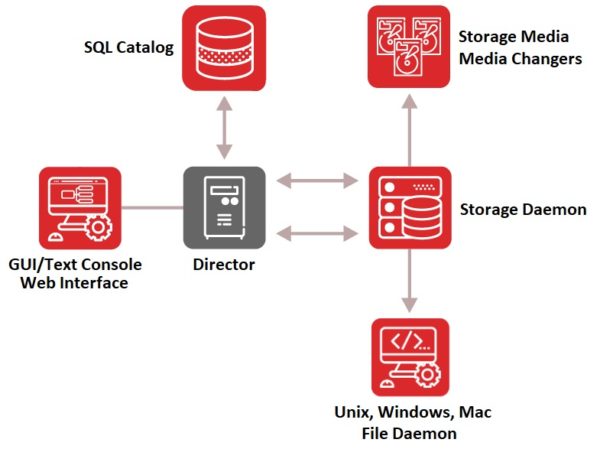
Bacula is unparalleled in the backup and recovery industry in providing for extremely high security levels. Of course, all backup vendors claim the same; however Bacula has demonstrable differences to its architecture and architectural flexibility that set it far apart from other vendors. This is the reason that the largest military organizations int he West choose Bacula over other solutions. Bacula’s ability spans specific elements regarding its architecture, features, usage approaches and customizability. Yet another important factor is that, unlike many other backup vendor solutions, Bacula’s critical components run on Linux.
Organizations rely on the trustworthiness of your backup vendor. With closed source software and services, all the trust is focused on a single entity, and most vendors do not provide any insight into the building blocks used that are not under their own full control. Back doors often exist to secretly harvest information from backup solution users without their knowledge or consent. With complex software programs, any user has to trust a great number of people involved in providing the software. Software users typically do not want to – or cannot – follow the long and convoluted chains of trust down to their origins. Bacula, among a world of software providing companies, can demonstrate that it is exceptionally trustworthy. This is because open source software, as is used by Bacula, allows users a better insight, has traceable trust chains, and encourages a culture of greater openness and explicit trust relationships.
Bacula is an especially powerful tool to identify any hostile modifications and report them, because modifications by intrusions will require changing some files, and traces of those changes will be left. This is when Bacula, when doing a backup, is able to notice such an incursion. Compared to other tools to detect file system changes, Bacula can do extensive checks that can also be adapted to the target platform for greater insight.